Node.js is a popular runtime for building fast, scalable web applications. But with its popularity comes increased security risks. Protecting your Node.js app is essential to safeguard user data, maintain trust, and ensure system integrity.
This guide outlines the most common security threats, such as injection attacks and XSS, and walks you through best practices to help keep your Node.js application secure.
Common Security Threats in Node.js
Understanding the common security threats is the first step in securing your Node.js application. We will cover some of the most prevalent threats you need to be aware of:
Injection Attacks
Injection attacks (such as SQL injection or NoSQL injection) happen when untrusted input is used to manipulate a database query. Attackers can gain unauthorized access, modify data, or even take full control of your system.
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) allows attackers to inject malicious scripts into web pages viewed by others. These scripts can hijack sessions, steal data, or alter site behavior.
Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) tricks a user into performing actions they didn’t intend to, such as changing account details or making transactions. For example, an attacker could create a link on a forum that, when clicked by a user logged into their bank, would transfer money to the attacker's account. CSRF exploits the trust a web application has in the user’s browser.
Insecure Dependencies
Using outdated or vulnerable packages and modules can expose your application to security risks. Attackers often target popular packages with unpatched vulnerabilities.
Best Practices for Securing Your Node.js Application
Input Validation and Sanitization
Always validate and sanitize user inputs to prevent injection attacks. In addition, use libraries, such asvalidator.js to ensure inputs conform to expected formats.
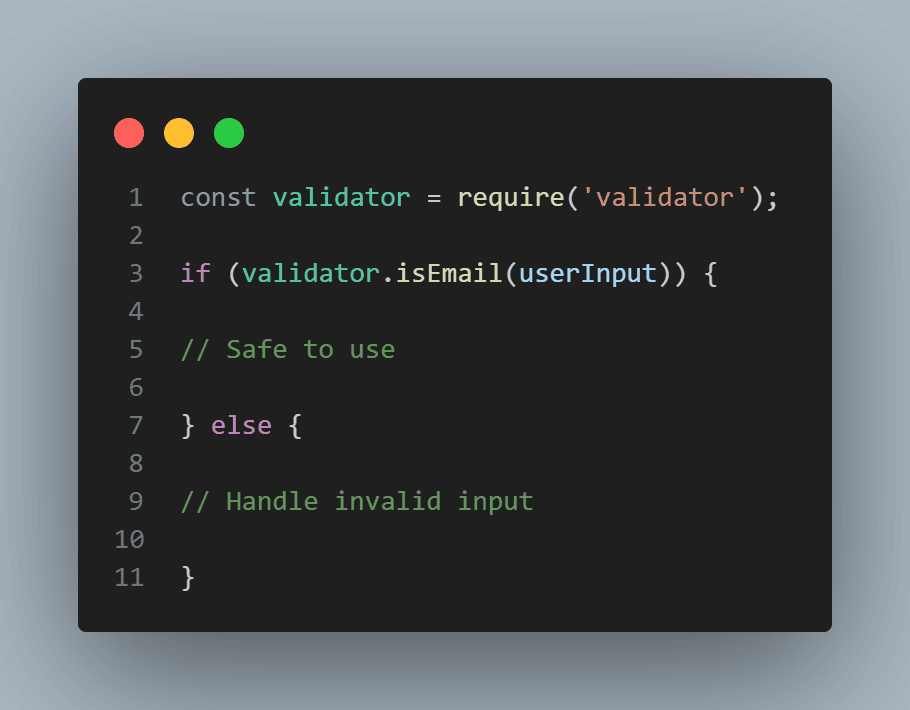
Use Prepared Statements
Avoid building dynamic queries. For SQL and NoSQL databases, use prepared statements to prevent injection attacks. Prepared statements ensure that user inputs are treated as data, not executable code.
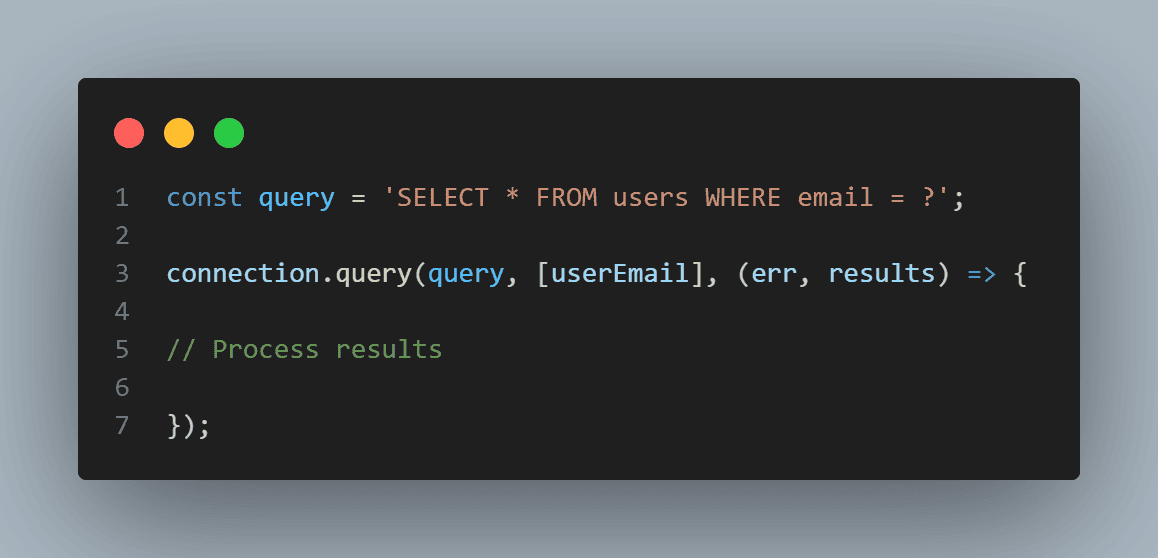
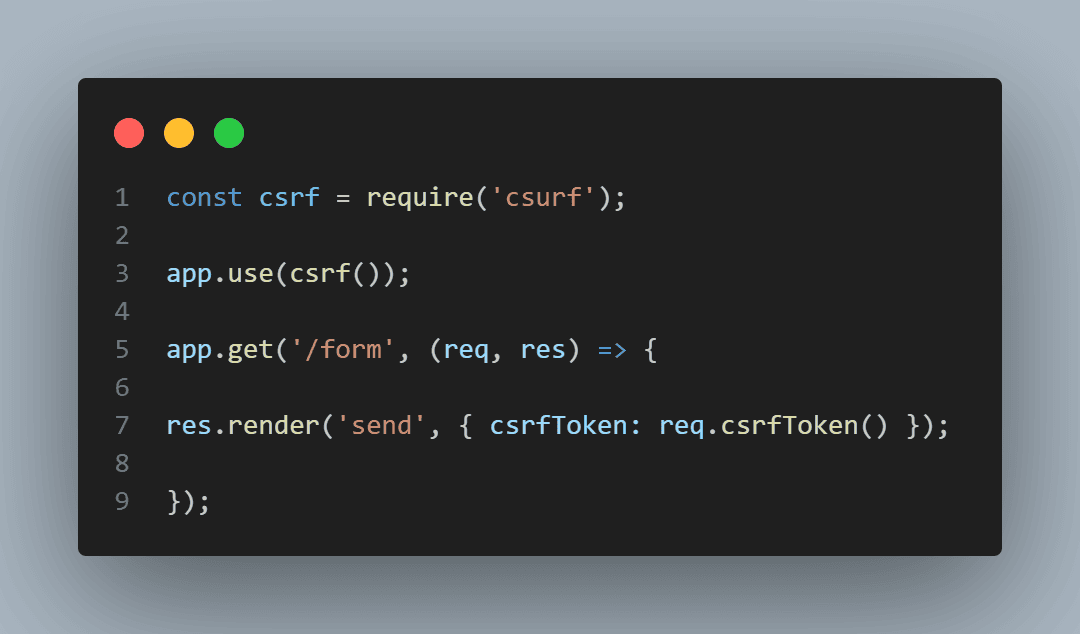
Use CSRF Tokens
Implementing CSRF tokens helps to protect against CSRF attacks. These tokens ensure that requests made on behalf of a user are intentional.
Regularly Update Dependencies
Keep your dependencies up to date to avoid vulnerabilities in outdated packages. Use tools like npm audit to identify and fix security issues in your dependencies.
npm audit fix
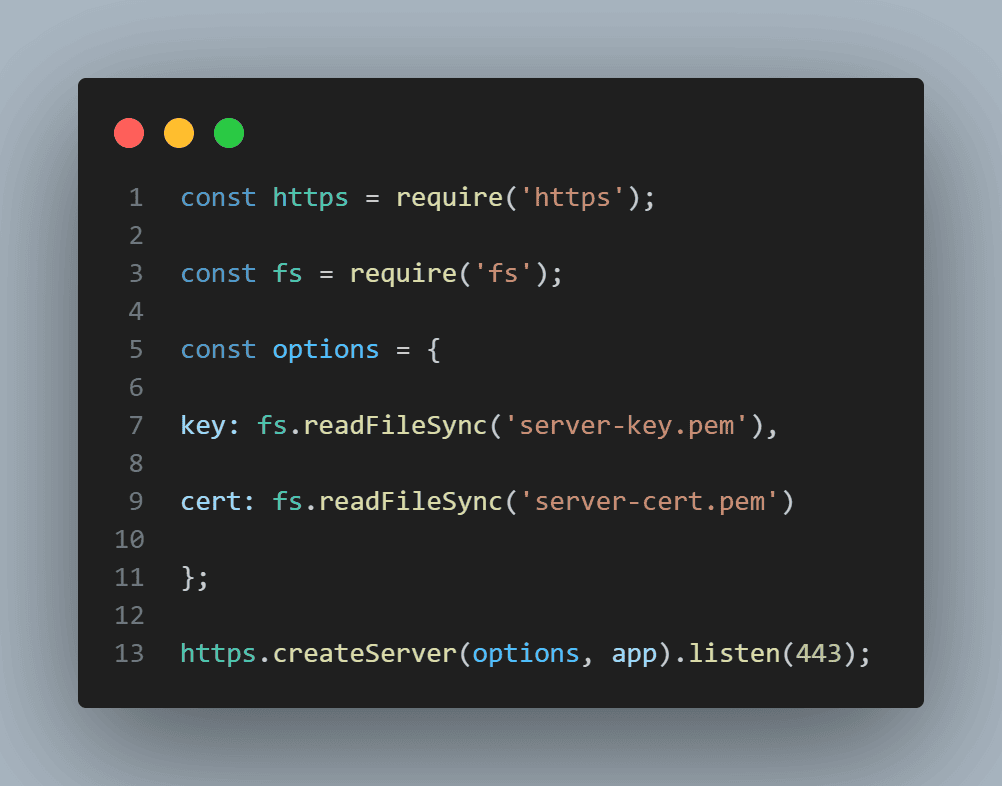
Use HTTPS for your Node.js application
Lastly, encrypt data in transit by using HTTPS. This prevents attackers from intercepting sensitive information between the client and server.
Enhancing the security of your Node.js application with Pipeops
Pipeops provides a robust logging and monitoring service to detect and respond to security incidents in real-time. By offering integrated observability features, it enables you to take immediate action and mitigate risks effectively. This gives a proactive approach that not only helps in identifying security breaches early but also assists in maintaining the overall health and performance of your application.
Conclusion
Securing your Node.js application isn’t a one-time task. It’s an ongoing process. By understanding common vulnerabilities and applying best practices like input validation, HTTPS, and dependency audits, you can significantly reduce your attack surface. Pairing these practices with robust monitoring tools like PipeOps gives you an extra layer of protection, ensuring you're not just reacting to threats, but actively preventing them.